
Leaky S3 Buckets:
How to Simplify Access
and Stop the Spill
by Rob Richardson
About Me

Rob Richardson is a software craftsman building web properties in ASP.NET and Node, React and Vue. He's a frequent speaker at conferences, user groups, and community events, and a diligent teacher and student of high quality software development. You can find this and other talks on https://robrich.org/presentations and follow him on twitter at @rob_rich.
Demo
Authenticating S3 Buckets
Securing an AWS Bucket
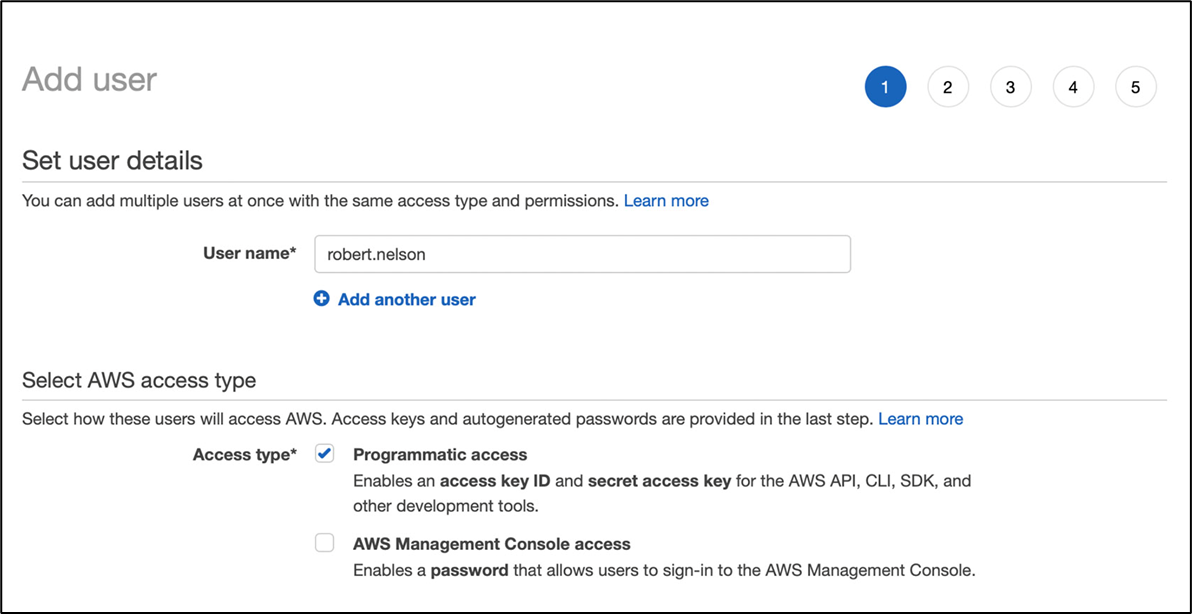
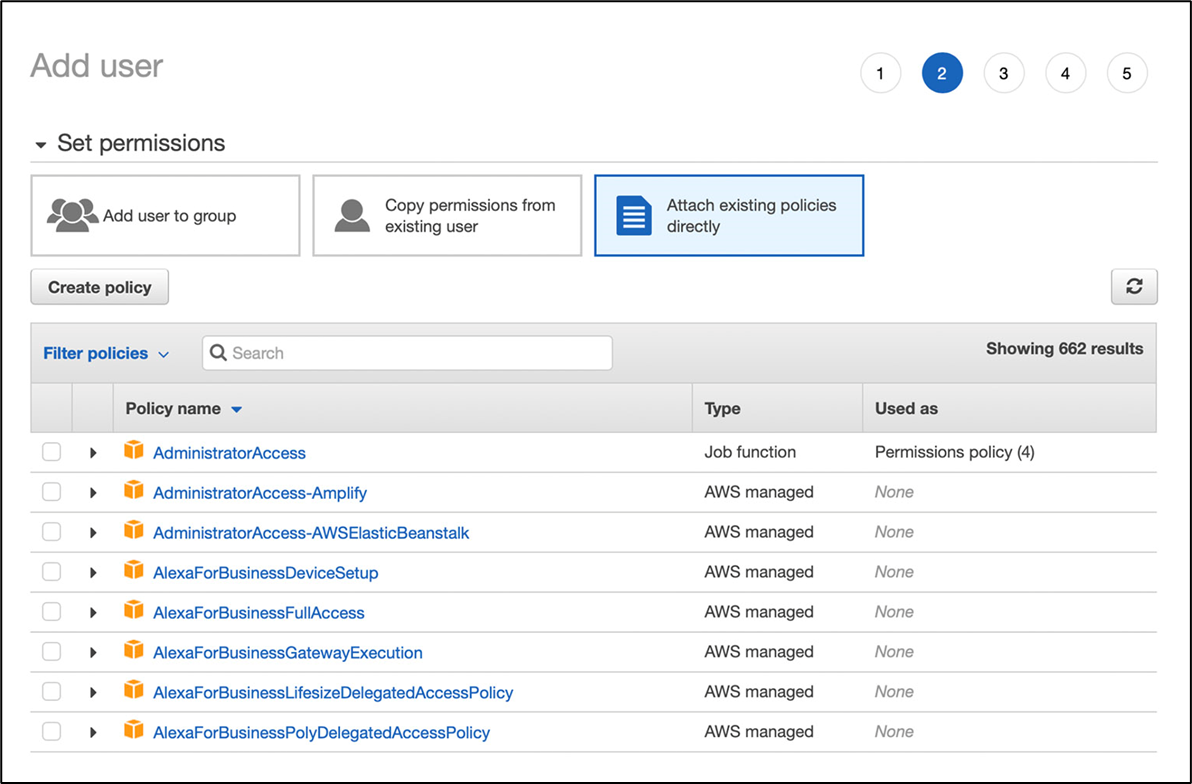
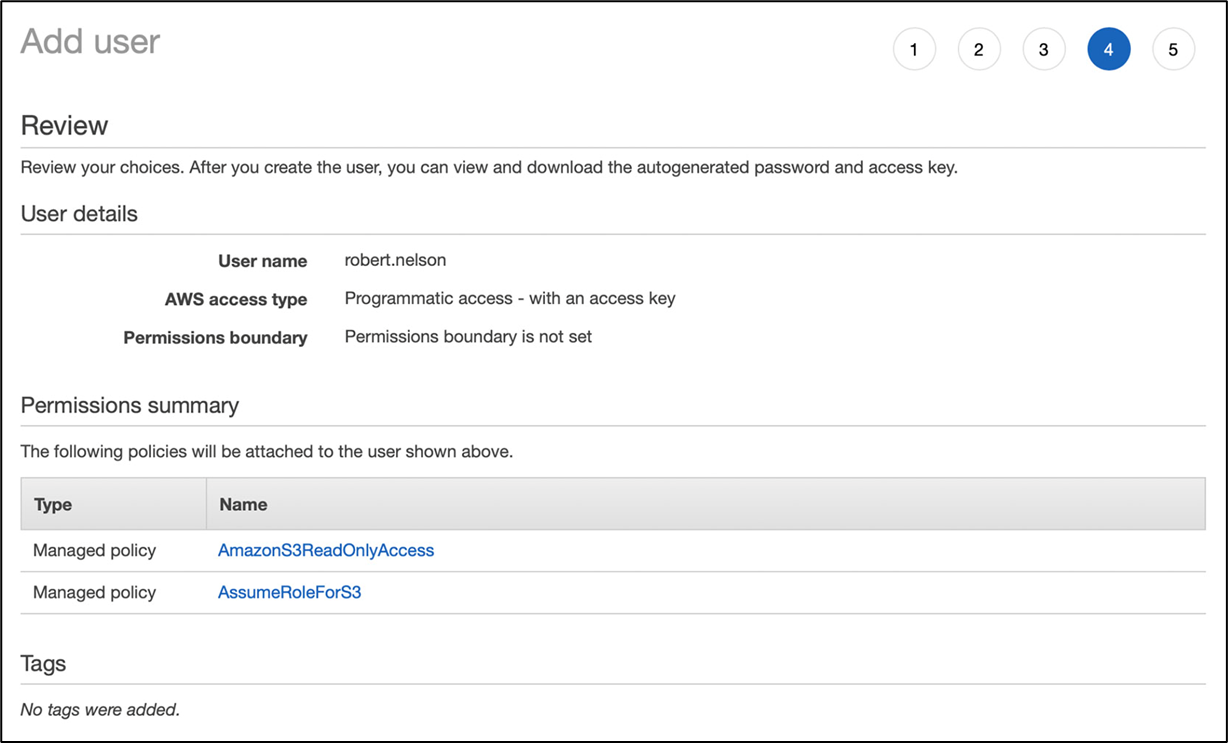
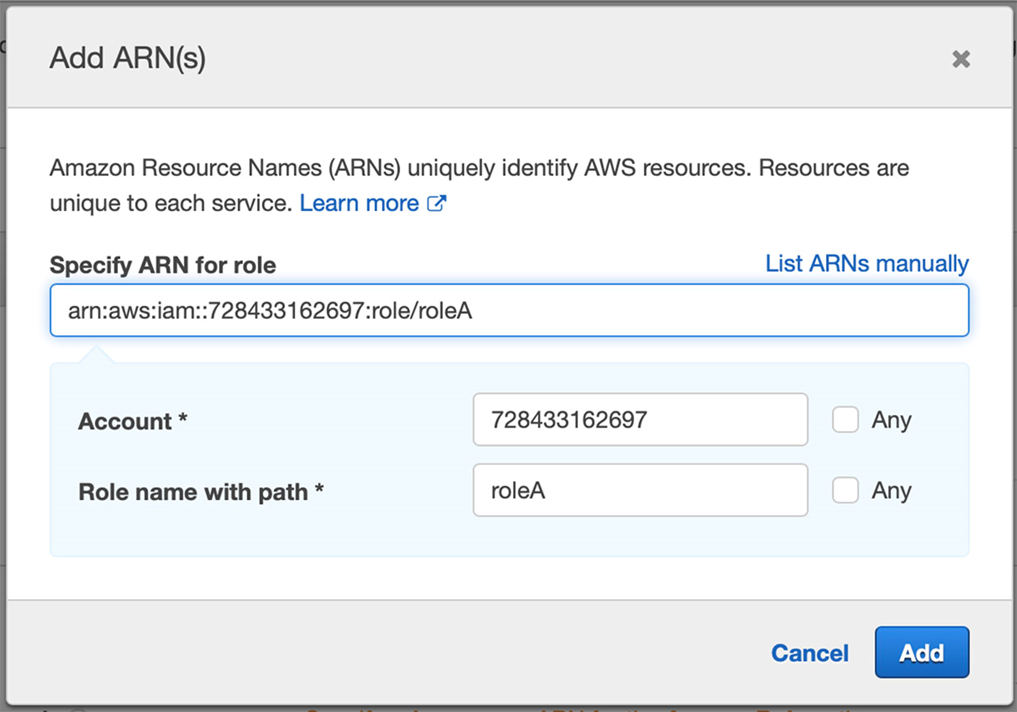
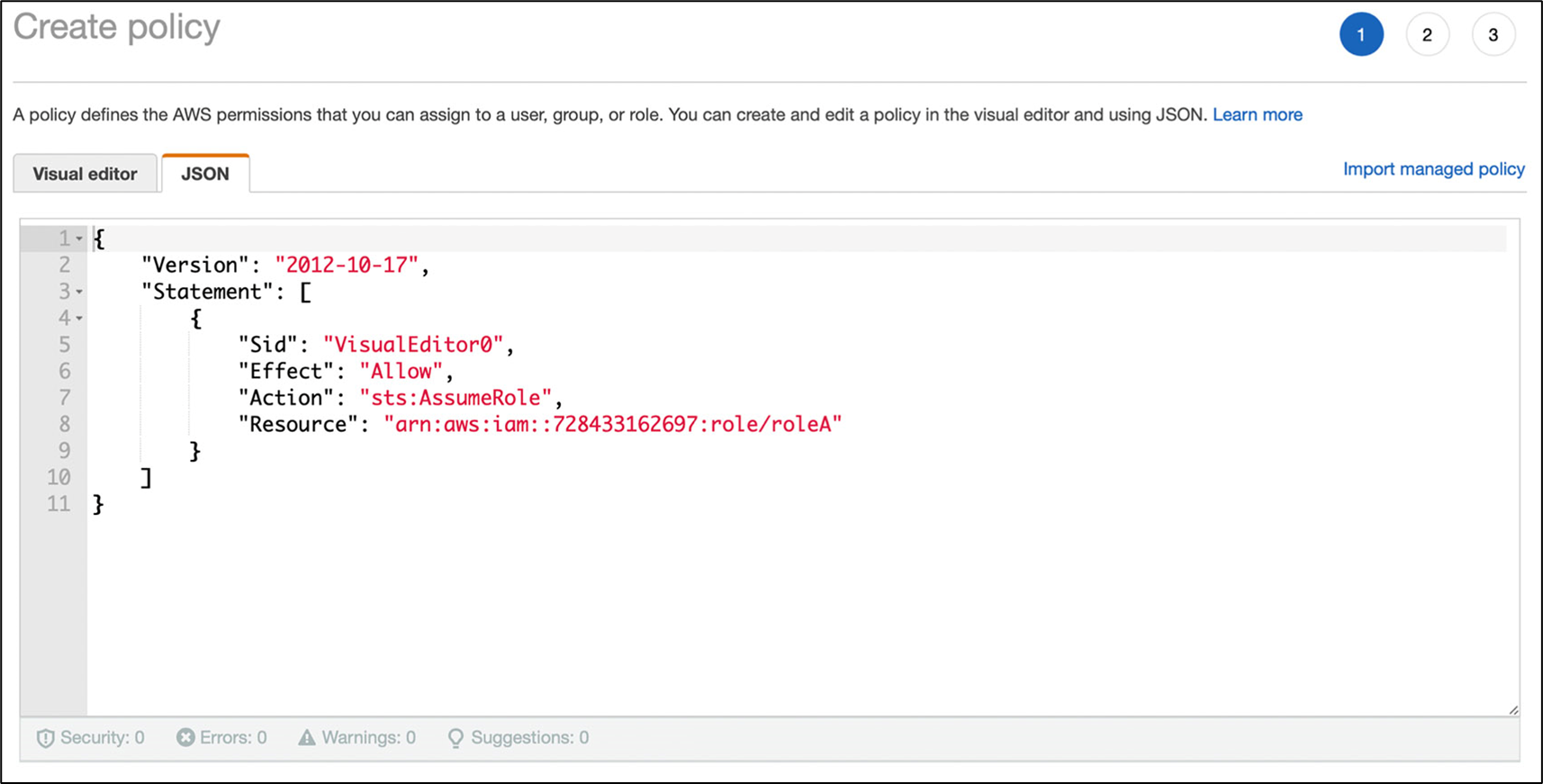
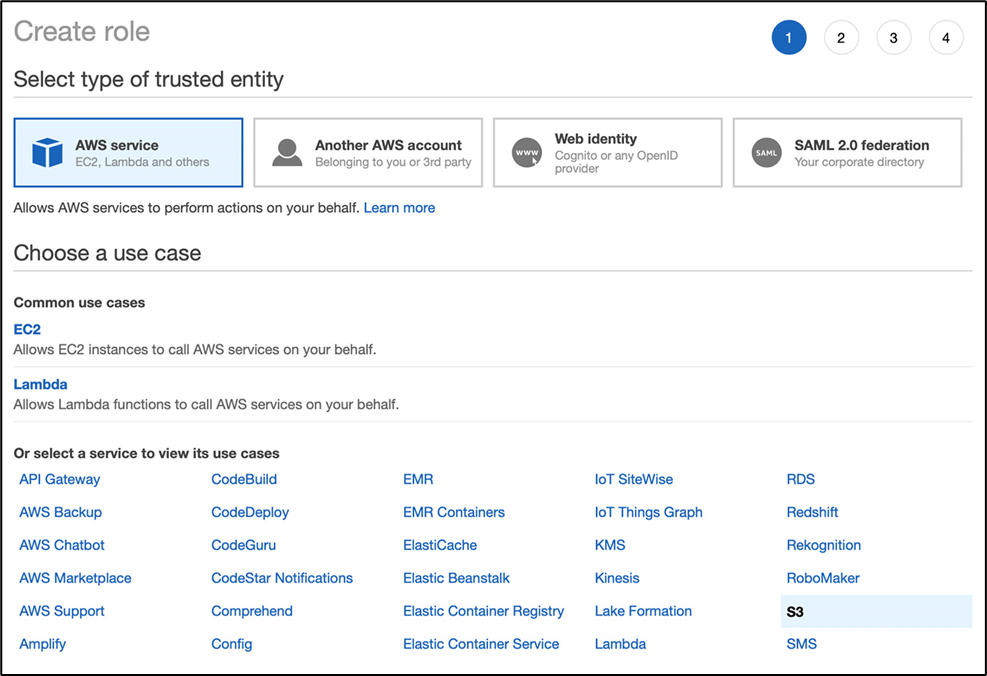
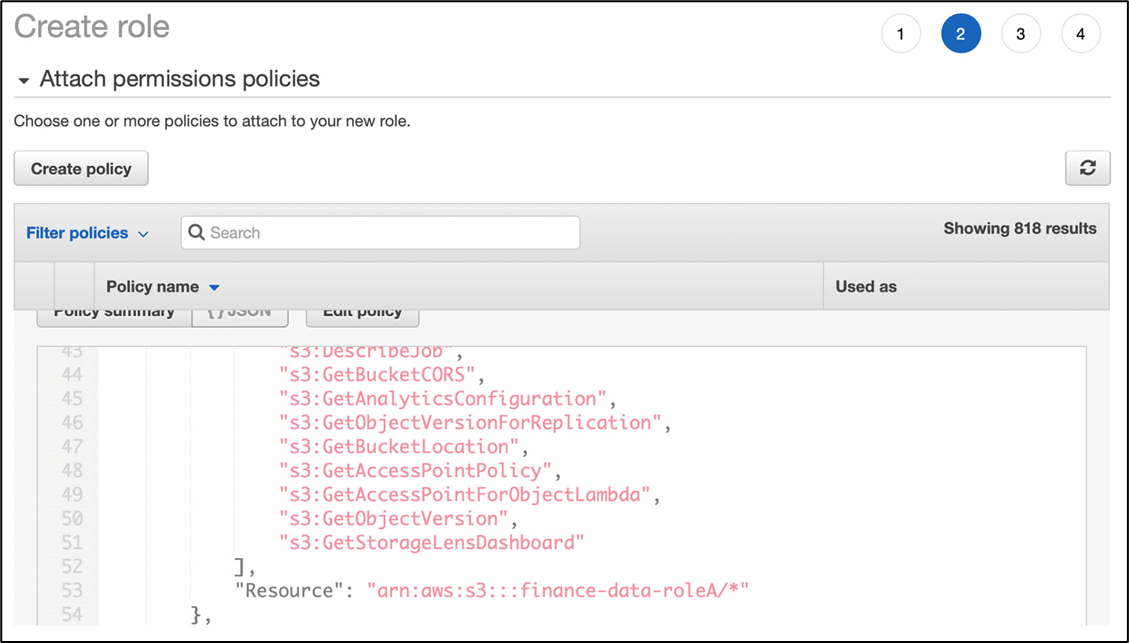
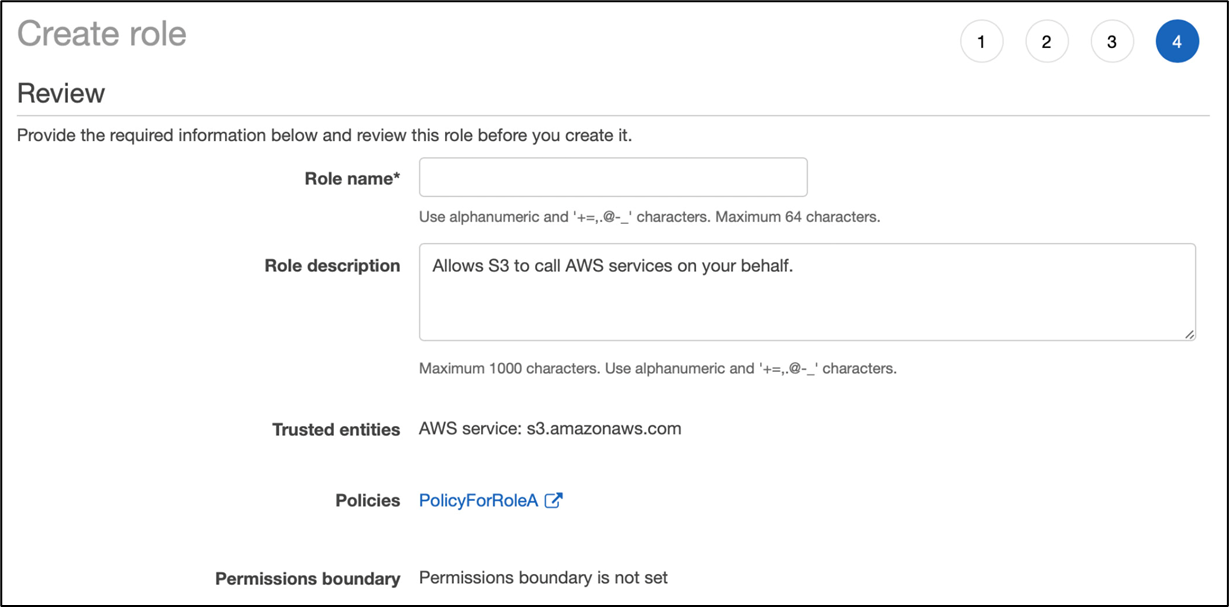
Many Policies
Technique:
Craft a new role, group, & policy for each use-case
Pros:
- Customize for specific use-cases
Cons:
- Difficult to configure consistently
- Too many roles, difficult to audit
One Policy for All
Technique:
Create a single, large one-size-fits-all role
Pros:
- Easy to apply
- Can define them globally
Cons:
- Can't opt-out specific buckets
- Difficult to apply consistently
- Must configure for the least secure use-case
S3 Access Logs
"Server access log records are delivered on a best effort basis. Most requests for a bucket that is properly configured for logging result in a delivered log record. Most log records are delivered within a few hours of the time that they are recorded, but they can be delivered more frequently. ... The completeness and timeliness of server logging is not guaranteed."
source: https://docs.aws.amazon.com/AmazonS3/latest/userguide/ServerLogs.html
Syncing Users and Roles

What do we want?
Let's Add Cyral
Cyral enables:

Federated Access Control
Authenticate where your users already are:

Federated Access Control
Cyral authenticates to your data stores:

Consistent Monitoring
Send access logs to:

Demo
The Cloud-Native Security for Data
Real-time Attack Response
Block data exfiltration before it happens

Cyral enables ...
the cloud-native
security platform for data.
- Real-time attack response
- Consolidated policies & monitoring
- Federated, temporal authentication